
Document Control & DRM: Stop Sharing, Copying, Printing, & Editing
Restricting document use with Safeguard PDF security
How to control access & use of a PDF document
Right-click on a PDF file, then in Safeguard Secure PDF Writer choose your DRM controls::
- Stop document printing, allow printing or limit the number of prints.
- Add dynamic watermarks to viewed and or printed pages. Dynamic variables replace actual user and system data when the document is viewed/printed so you only have to protect the document once for all users.
- Make the PDF expire on a fixed date, after a number of views, after a number of prints, or after a number of days from opening.
- Stop screen grabbing applications (even from remote connections) and prevent the use of Windows printscreen.
- Track document views and prints.
Safeguard’s default document control
- Prevents modification and editing
- Stops copying and pasting of content
- Stops forwarding – locks PDF files to specific devices to stop sharing
- Optionally lock document use to locations on a user or global basis
- Revoke documents at any time regardless of where they are located
- There are no passwords for users to enter, manage, or remove

 DID YOU KNOW?
DID YOU KNOW?
Adobe PDF permissions are totally useless
- They can be instantly removed using PDF password removers
- Permissions can be easily bypassed using a Mac
- Permissions can be removed using Google Drive
- Third party PDF readers can ignore these controls
“We were using varying levels of PDF password protection before finding Locklizard. Unfortunately, once the PDF file was distributed, the password could be shared among users so it provided little in the way of protection. Also, there was nothing to stop users removing the permissions we applied such as restricting editing or preventing printing.
We would definitely recommend both Locklizard and Safeguard PDF Security. Locklizard provide a great service and product at a very reasonable price.”
 Using DRM to control document use: prevent sharing, forwarding, copying, printing, editing
Using DRM to control document use: prevent sharing, forwarding, copying, printing, editing

Many people think that encrypting a document stops it from being stolen. And they are right – but only whilst it stays encrypted. That’s why hackers never attack SSL, and always attack the endpoint when the secrets have been revealed.
The point of DRM is that it controls what happens next – what the recipient is licensed (allowed) to do with the information after it arrives. It’s this that makes DRM a much more powerful tool than encryption for controlling document use.
 Prevent forwarding and stop sharing
Prevent forwarding and stop sharing
As everyone (especially the music and film businesses) knows, it is not easy to prevent a document from being forwarded or stop unauthorized sharing. Torrent sites, for example, encourage forwarding and sharing as their only objective. Unless you apply additional protection, a recipient can do whatever they like with a document once it is decrypted – including uploading it to a file-sharing site. So how do you prevent a document from being shared?
Typical DRM controls stop forwarding by making sure that only encrypted files can be forwarded. Unless the recipient has the key to open the file they cannot do anything with it. Locklizard-protected files are always encrypted with secret keys (not disclosed to the user) to stop file forwarding from being successful.
To further prevent a document from being shared, a DRM system will prevent a recipient from being able to transfer their own license to use the file by locking it to an authorized device. If this is not done, then the license can be passed from one user to another (rather like a password can).
You can use licensing controls to strengthen DRM even further and prevent PDF sharing by restricting use to specific locations. For example, if a user takes their device home with them, they will not be able to view protected content until they return to the office.
 Prevent copy and paste
Prevent copy and paste
Another key requirement of any DRM system is to stop sharing by preventing a document from being copy and pasted. This may be by making content un-selectable, disabling the use of any copy command, or by ensuring that any pasted content is overwritten in memory so it is not usable.
You must also prevent screen grabs, otherwise users can take high-quality screenshots with screen-grabbing applications. This includes preventing screen grabs from remote connections – a common workaround technique.
If you do not prevent a document from being copied and pasted, then anyone opening a document can transfer the contents out into another application (Word, image editing, publishing package, etc.), either a screen at a time or many screens using automated screen capture tools.
 Document print control
Document print control

A major weakness in document control is printing, since users can print documents and send them to others.
If you allow PDF printing for example, then it is possible in most PDF viewing software for the user to ‘print’ to a PDF driver and create an unprotected PDF file which can then be distributed to anyone.
Obviously, one way to prevent printing is to disable printing in the application. But stopping users from physically printing (and therefore being able to create a scanned copy) may not be practical. You may have to allow printing inside of a business for various reasons. It is also essential, then, that you can control printing as well as stop output to a printer altogether.
If you cannot prevent a document from being downloaded and printed, you must take other steps to prevent sharing and the forwarding of printed copies. Using DRM, you can prevent use of file drivers, which is more elegant than acting to disable printing entirely. A user has to go to the effort of scanning the document back in and saving it to a file before they can distribute it to others. It will be lower resolution and missing links and other embedded content.
 Watermarks in aiding document control & preventing sharing
Watermarks in aiding document control & preventing sharing

Printing and sharing controls go a long way, but they cannot protect documents in every situation. One example is the scenario presented above, where an organization needs to allow printing but has no real technical route to prevent users from creating scanned copies. Another type of copying that cannot be directly prevented is the use of a phone or camera to take a picture of a screen. This is where watermarks come in.
 Print watermarks
Print watermarks
Having even low-quality scanned copies floating around is not ideal. The obvious step to combat this is to add non-removable dynamic watermarks to the printout. This does not stop printing and scanning, but it can link the identity of the user to the document. You would be surprised how quickly somebody changes their mind about sharing a document when it has a watermark with name on it, especially if it is available for download from the Internet.
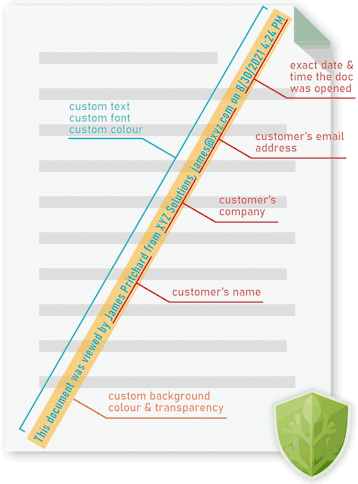
Locklizard Safeguard allows you to insert custom text or image print watermarks that cannot be removed. Document publishers only need to protect a document once to insert watermarks that are unique to each user who prints the document. Variables like %UserName% and %Email% are replaced with the user’s information at print time to increase the personal risk associated with leaking documents.
To learn more about secure document printing, see print management security & printing documents securely.
 View watermarks
View watermarks
Dynamic view watermarks follow in a similar vein as print ones but are designed to prevent non-typical screen copying such as phone photographs. They are therefore added separately to print watermarks, with the ability to use different text, font, locations, etc. to better suit the screen.
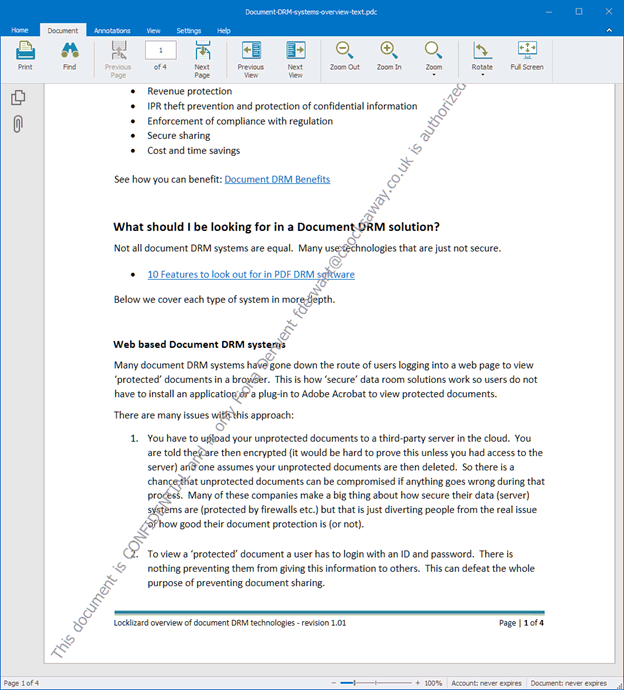
Whatever the choice, protected documents with the %UserName% variable (for example) will always show the user’s name, regardless of the device or location they are opening it from.
 Prevent document editing
Prevent document editing

Watermarking starts to fall apart if you do not have a mechanism to prevent a document from being edited. If a user can edit your document, then they can delete your watermarks and potentially modify the document to remove other security restrictions. Most PDF applications, for example, are multi-purpose, designed to work as both a PDF viewer and a PDF editor. The problem with this approach is that’s very prone to abuse. As the document must be decrypted to provide an experience that isn’t unusably slow, content can be easily extracted via a variety of methods. In the case of Adobe Acrobat, it’s as simple as opening it in an application that doesn’t respect its editing controls.
Locklizard DRM can prevent PDF editing by using an encrypted file format that can only be opened in its secure viewer application. The viewer does not include the ability to edit to begin with, and document content is only ever decrypted in memory so that it cannot be extracted. As Locklizard also prevents copying and pasting, screen grabbing, and printing to file drivers, users also have no route to paste its content into another application and edit it there.
 Secure document disposal & self-destructing files
Secure document disposal & self-destructing files

Another vital component of document control is what happens to them once they reach the end of their lifecycle and version control for documents in circulation. Documents must be regularly phased out of a business for various reasons, from data retention laws, to a new revision due to errors or obsolete documents.
Deleting every copy of a document, however, is not trivial. Files can be copied an infinite number of times. Every document uploaded to a cloud platform, sent in an email, or copied to a USB drive is another file that needs to be destroyed. That’s why it’s better to make inaccessible not the file itself, but the content inside it. By removing the ability for users to decrypt a document, you make it completely useless. This is the approach that Safeguard PDF DRM takes.
Locklizard Safeguard enables secure document disposal on a per-user or global basis, supporting the following revocation methods:
- Revoking access to a document for all users or a specific user immediately
- Revoking a document after the user reaches a certain number of prints or views
- Self-destructing the file on a fixed date or a number of days since the first open
Unlike expiry scripts where disabling JavaScript renders them useless, and other ineffective methods, Locklizard’s document expiry cannot be bypassed by disabling functionality or changing the date on your computer. You can choose to check the document’s validity against the licensing server either:
- Whenever it is opened
- Every x days
- After x days and never again
- Only when an internet connection is available
This provides the document controller with the flexibility to choose whichever method works best for a particular document’s use case. Due to the anti-copying controls mentioned above, users are also unable to make an unsanctioned copy that cannot be revoked.
 Secure Document Distribution
Secure Document Distribution

It’s just a simple fact that most documents inside of a business will be shared internally or externally at some point in their lifetime. For many documents, this is not a big deal as they will not cause damage should they leak. For information that is sensitive or confidential, however, it is necessary to ensure that documents are not intercepted and can only be viewed by authorized parties.
The former is quite easy to arrange. Simple file encryption will ensure that files remain useless to those without a decryption key when they are in transit and at rest. The difficulty comes in controlling what happens after an authorized user decrypts the file. Without additional protection, they can share the decrypted format with whomever they like, leaving you none-the-wiser.
As a result, the best way to share documents securely is by encrypting them with a DRM solution first. This will both protect the document in transit/at rest and ensure that the document cannot be shared by authorized users once it’s in use.
Other solutions, such as secure data rooms or cloud storage services, are not able to provide this functionality as their browser-based nature makes them too easy to manipulate. Traditional access control and ERM solutions, meanwhile, are designed for sharing internally and are therefore cumbersome or impossible to use with third parties such as accountants, lawyers, etc.
Locklizard protected documents can be distributed just like any other file – added to your document management system, uploaded to a website, emailed, etc.
 Document tracking
Document tracking

Some document control software also provides admins with the ability to track and audit document use. With the ability to track opens and prints able to aid with compliance, timely deal closure, and ebook usage insights, to name a few.

The most important thing to remember is that a document tracking system that cannot prevent copying is next to useless. If users extract content unprotected to another location, then you can no longer track their use effectively. Also, if users can share login credentials to online systems then you have no idea who you are really tracking.
This is another reason why having a DRM solution, which is designed from the ground up to prevent copying and unauthorized use, is the best choice for document control.
 Download Document DRM software for total document control: restrict access, control use
Download Document DRM software for total document control: restrict access, control use

Prevent copying, sharing, printing & editing with Locklizard DRM software
Download DRM software that uses digital rights management (DRM), US Government approved AES encryption and licensing to control access and use of your documents regardless of their location.
With Locklizard DRM software you can control document access and what authorized users can do with them, add dynamic watermarks and track use.
See our DRM technology to see why Locklizard document security provides greater protection for your documents than solutions that use passwords or plugins.
View our customer testimonials or read our case studies to see why thousands of organizations use Locklizard DRM software for effective document control to prevent sharing and copying of their documents.









 Free Trial & Demo
Free Trial & Demo DID YOU KNOW?
DID YOU KNOW?
 Using DRM to control document use: prevent sharing, forwarding, copying, printing, editing
Using DRM to control document use: prevent sharing, forwarding, copying, printing, editing Prevent forwarding and stop sharing
Prevent forwarding and stop sharing Prevent copy and paste
Prevent copy and paste Document print control
Document print control Watermarks in aiding document control & preventing sharing
Watermarks in aiding document control & preventing sharing Print watermarks
Print watermarks View watermarks
View watermarks Prevent document editing
Prevent document editing Secure document disposal & self-destructing files
Secure document disposal & self-destructing files Secure Document Distribution
Secure Document Distribution Document tracking
Document tracking Download Document DRM software for total document control: restrict access, control use
Download Document DRM software for total document control: restrict access, control use FAQs
FAQs















