ISO 9001 and Document Security

ISO 9001 Document Control Requirements & Protecting Documented Information
Learn what ISO 9001 is, why it is important, and how to meet its requirements for document control using digital rights management software.
ISO 9001 / ISO9001 certification

ISO 9001 lists a broad range of requirements that organizations must apply with in quality management system to be compliant. This blog, will address what is required from a document security perspective, covering:
- What is ISO 9001?
- How to get ISO 9001 certified
- What are the ISO 9001 requirements for document control?
- Why is document control important for documented information?
- Ensuring adequate protection against improper use
- How Locklizard Safeguard can aid ISO 9001 compliance
 What is ISO 9001?
What is ISO 9001?

ISO 9001 is an international standard that outlines general requirements for quality management systems (QMSs). It helps to enable worldwide consistency in QMSs while allowing organizations to demonstrate that they meet customer and regulatory expectations regarding quality, process, and security.
The five main elements of the standard are:
- Leadership
- Planning
- Support
- Operation
- Performance evaluation
Organizations that are compliant with ISO 9001 can benefit from increased customer satisfaction, operational efficiency, credibility, better risk management, higher employee engagement, and a competitive advantage in their marketplace.
Importantly, though, ISO 9001’s requirements are generic – organizations are expected to adapt them to the context of their use case and the needs of interested parties.
 How to get ISO 9001 certified
How to get ISO 9001 certified

The general ISO certification process is as follows:
- Buy the latest version of the ISO 9001 standard and learn its requirements.
- Conduct a gap analysis to compare your existing processes against ISO 9001 requirements.
- Implement the required processes and document them securely.
- Train employees on the requirements and new process additions.
- Conduct an internal audit to evaluate the QMS and address non-conformities.
- Choose and accredited certifier to audit you’re your QMS.
- The certifier will perform a stage 1 assessment where they review your documented QMS and highlight possible improvements and gaps.
- The certifier will complete a stage 2 assessment on-site and through employee interviews.
- If there are changes required for conformity, you correct them and provide evidence of your remediation. The certified may perform a follow-up audit.
- Once you meet all of the requirements the body will issue a certificate, which is a valid for three years.
It’s important to understand that just because you receive certification, it does not mean your work is done. The certifier typically performs periodic surveillance audits to ensure ongoing compliance. Continual process improvement to address new risks, market conditions, regulation updates, and more may be required to maintain compliance.
 How many US companies are iso 9001 certified?
How many US companies are iso 9001 certified?
As of 2023, there were approximately 837,052 valid certificates worldwide, 26,833 of which were in the United States. The industries with the largest number of certifications in the US are as follows:
- Basic metal and fabricated products: 4292
- Electrical and optical equipment: 2166
- Machinery and equipment: 1184
- Wholesale trade and repairs of motor vehicles, motorcycles, and personal and household goods: 1165
- Engineering services: 789
 What are the ISO 9001 document control requirements?
What are the ISO 9001 document control requirements?
![]()
There are various requirements for document control in ISO 9001, but, in general, the key ones are:
- Document identification: Each document should be easily and uniquely identifiable (i.e. title, number, date).
- Approval and review: Documents should be approved by authorized personnel before use. The organization should periodically review documents to ensure they’re current and effective. They should go through the approval process each time there are significant changes.
- Controlled distribution: Documents should be made accessible to those they need them while being managed to prevent unauthorized access or the use of outdated versions.
- Store documents securely: Protect against damage, loss, and hacking, and define a retention period after which documents expire.
- Ensure adequate protection against improper use: Ensure changes to documents are authorized and documented and maintain a history of revisions (version control).
- Document management: Establish a procedure for managing documents and ensure your document management system supports the requirements outlined above (version control, access control, expiry, etc.)
 Requirements for documented information of external origin
Requirements for documented information of external origin

It’s important to remember that ISO 9001 states that you should make special considerations for documents of an external origin. Specifically, it states:
“Documented information of external origin determined by the organization to be necessary for the planning and operation of the quality management system shall be identified as appropriate and controlled”.
This is vague, but the gist is that you must implement measures to control external documents as well as internal ones, for example, by maintaining a register, establishing a clear process, and controlling access and distribution.
 | Why is document control important for documented information? |

ISO 9001:2015 states that document information should meet the following four main objectives:
- Communication of information: Documentation communicates information about the organization’s processes and systems, with specific steps on how to adequately perform them.
- Evidence of conformity: Proof that what was planned has actually been done.
- Knowledge sharing: To preserve the organizations’ experiences, for example a technical specification that can used as a template for design and development or new apps.
Document control is crucial to meet many of these objectives. For example, it is difficult to give evidence of conformity if you cannot verify that somebody hasn’t tampered with the files. But document control is not just important to meet ISO standards. It helps to ensure that information is accurate and reliable, consistent and standardized, and traceable and auditable. It also prevents document leaks which could damage the business.
So, how do you ensure that your documented information has adequate protection against improper use?
 Ensuring adequate protection against improper use
Ensuring adequate protection against improper use

You want to ensure that you control distribution access, retrieval and use of your documented information while keeping a version history, protecting it from unintended alterations, and enabling document retention and disposition.
This is not necessarily trivial using common solutions. We’ll cover what is required to effectively enforce them, as well as some common solutions that might not be good enough.
 Version control
Version control
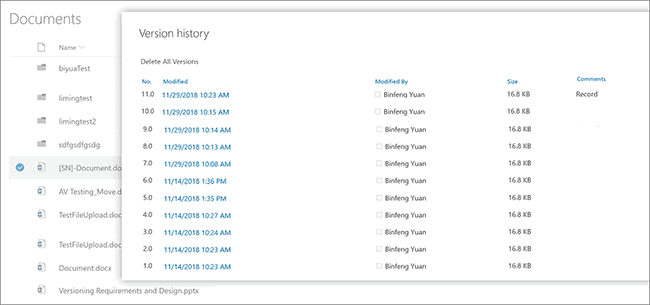
Version control is relatively easy to implement, but there are a few things you need to do to ensure that it is accurate and reliable. Firstly, you must protect the integrity of documents so that people cannot alter previous versions. You also need accurate audit trails that track who has made what changes to a document and when. Accurate audit trails, of course, require a way to be sure a user is who they say they are and that they cannot cover their tracks.
 Protection from unintended alterations
Protection from unintended alterations
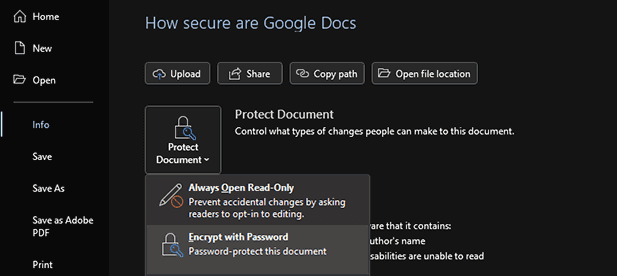
Organizations can prevent unintended alterations with rudimentary security. Features such as Microsoft Word’s read-only mode, Adobe PDF encryption or PDF password protection, or Google Docs view-only sharing are all suitable for this, though they may compromize security in other areas.
 Retention and disposition
Retention and disposition
Retention and disposition are a little more difficult to implement with certainty. Firstly, you need your anti-copying controls to work, or else users will create unprotected copies you cannot dispose of. Locking all copies to on-premises devices is one way of achieving this, but this is rarely practical if you have a remote workforce or work with external third parties.
An ideal solution does not try to track down and delete every copy of a document. Instead, it would dispose of documents regardless of where they are located by enforcing strong anti-copying controls and overwriting the documents’ decryption key. No valid encryption key and no copies means no access.
 Distribution, access, retrieval, and use
Distribution, access, retrieval, and use
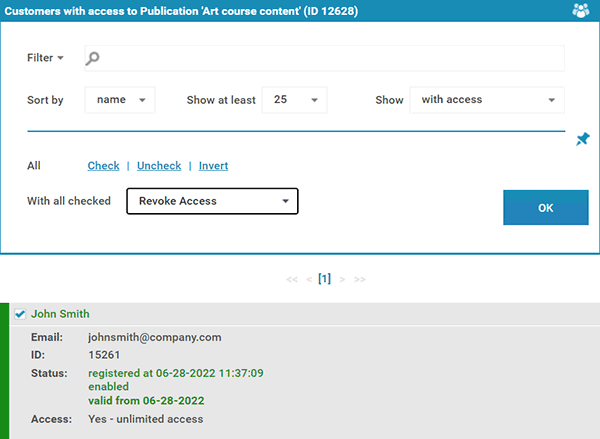
A cloud document service such as Google Docs or a secure data room is the most popular way to enforce document access, distribution, and retrieval. Access is enforced by providing authorized users with a username and password, and distribution can typically be limited to those within the organization by the admin. Use is controlled by JavaScript in the browser, which disables print, editing, and copy-paste functionality if a user shares a document with “View-only” rights.
Though we can’t comment on whether they would meet ISO standards, these methods are rarely successful.
- There is nothing to stop users from sharing their login info with others – whether intentionally or because they have been socially engineered or phished.
- Two-factor authentication, while useful for preventing accidental password sharing, does not stop intentional sharing, as the user can provide their authentication code, too.
- Users can share protected documents with unlimited users by using screen sharing apps – i.e. giving access to an online meeting (Zoom, Microsoft Teams, Google Meet, etc.), or by giving full control of a system via remote desktop tools.
- Users can automate screen grabbing using a plugin that saves screenshots to PDF (Fireshot Pro for example). Watermarks can then be easily removed using AI PDF watermark removers.
- JavaScript editing/copying controls, meanwhile, are usually easy to bypass as the browser does not have sufficient control over a user’s system. We cover this in detail in how secure are Google Docs.
To prevent unauthorized distribution, access, and use with certainty, you need the following:
- Strong encryption, with decryption keys that the user cannot share to grant access.
- An application or service that can limit the system functions in the document (for example, printing and screenshot apps and remote screen sharing).
- A licensing system that locks access to devices rather than usernames and passwords (which can be shared).
Importantly, in the case of ISO standards, you need to be able to enforce these on external parties if you receive documented information from them.
 How Locklizard Safeguard can aid your ISO 9001 certification
How Locklizard Safeguard can aid your ISO 9001 certification

Locklizard Safeguard is a PDF DRM solution that can help organizations achieve ISO 9001 compliance by ensuring that their documents cannot be subject to unauthorized sharing, editing, printing, copying, saving, screen sharing and screenshots. It features:
- Irremovable saving, copying, printing, screenshotting, screen sharing and editing controls.
- Dynamic, irremovable watermarks that can contain the user’s name, company, and more.
- Expiry based on a date, number of times since first opened, number of views, or number of prints, regardless of where the file is located.
- Revoke documents or users instantly, even after distribution.
- Control distribution and access with AES encryption and a secure licensing system.
- Automatically sign a unique ID to each PDF.
- Lock documents use to locations (for example, the office only).
- Track who is viewing/printing and document, when, and where from for a clear audit trail.
Locklizard’s API and command line tools allow you to easily integrate it into your existing QMS systems and processes for complete protection of your PDF documents. Take a free trial of our DRM software to see if it works for you.
 FAQs
FAQs

What does ISO 9001 / ISO9001 stand for?
ISO 9001 stands for the international standard for standardization, with the code 9001 referencing the standard for quality management systems.
What document naming convention or document numbering system should I use for iso 9001?
There are no set naming conventions; the standard only states that documents should be easily identifiable. The most practical way to implement this, however, is by adding a reference number or similar as a suffix or prefix to the file title. If you want to go further, you can add an identifier for the department or document type to the suffix — for example, HR1273.
What are the four levels of documentation for ISO 9001?
The four levels of documentation for ISO 9001 are as follows:
- Quality policy: A top-level document stating the organization’s commitment to quality and its overarching quality assurance objectives.
- Quality manual: A document outlining the structure of the Quality Management System (QMS), detailing the scope, processes approach, and interactions within the system.
- Procedures: Documents describing the methods and responsibilities for specific processes within the organization, ensuring consistency and compliance.
- Work instructions and records: Detailed, step-by-step guidance for performing specific tasks (work instructions) and evidence of activities performed and results achieved (records), demonstrating compliance with the QMS and ISO 9001 standards.
Is ISO 9001 a legal requirement?
No, it is simply a voluntary, internationally recognized standard. However, there may be some crossover between the recommendations in ISO 9001 and local laws or customer requirements. Complying with regulatory requirements is essential for compliance and the general effectiveness of the organization and in meeting customer expectations.
Is ISO 9001 worth it?
It depends on many factors, including your industry, the ISO status of competitors, your revenue, and the context of the organization. Obtaining ISO 9001 certification means the implementation of good quality management principles, which leads to tangible business benefits for companies of any size. However, high initial costs and the need for continuous improvement and investment mean it is not feasible for every organization.
If a document cloud collaboration system is ISO 9001 certified, does it mean it is secure?
No. Google Workspace, other document collaboration solutions, and secure data rooms have multiple certifications including ISO 9001, but their security can be easily bypassed using simple methods. See for example Docsend2PDF which converts a Docsend protected document to an unprotected PDF file and Google Docs security.
No cloud based web viewer solution can prevent sharing of login details, simple screen sharing, or screen grabs. Even if screen grabs are ‘prevented’, users can resize the browser window (to remove focus) and then screen grab using screen grabber software.

 What is ISO 9001?
What is ISO 9001? How to get ISO 9001 certified
How to get ISO 9001 certified How many US companies are iso 9001 certified?
How many US companies are iso 9001 certified? What are the ISO 9001 document control requirements?
What are the ISO 9001 document control requirements? Ensuring adequate protection against improper use
Ensuring adequate protection against improper use Version control
Version control Protection from unintended alterations
Protection from unintended alterations Retention and disposition
Retention and disposition Distribution, access, retrieval, and use
Distribution, access, retrieval, and use How Locklizard Safeguard can aid your ISO 9001 certification
How Locklizard Safeguard can aid your ISO 9001 certification FAQs
FAQs
