GDPR: Data protection & document security

GDPR’s data security requirements & how to achieve GDPR-compliant file sharing
Though GDPR came into effect several years ago, it’s still causing plenty of pain. New businesses must figure out how to protect sensitive personal data to a high standard or risk huge fines. This requirement includes not only data at rest but also sending documents securely, keeping sensitive data under your control, and complying with GDPR policies such as data retention. Thankfully, though all this sounds intimidating, it’s easier to achieve than you think.
 GDPR and data security
GDPR and data security

A lot of interest was generated by the EU introduction, back in May 2016, of GDPR, which introduces explicit requirements on organizations that collect and process personal data. Though businesses had several years to prepare for GDPR’s application in 2018, there was and still is confusion regarding how to send documents with such data securely while complying with GDPR.
Though we will soon get into that, it is worth first explaining the basics of GDPR: its requirements, what constitutes personal and sensitive data, and the provisions surrounding data retention.
 GDPR: What information needs to be secured?
GDPR: What information needs to be secured?

To ensure compliance with GDPR, any information relating to an identifiable person needs to be secured appropriately.
 What is personal data under the GDPR?
What is personal data under the GDPR?

The definition of personal data under GDPR may be broader than you expect. It is important to understand that the regulation does not look at data in a vacuum: any data relating to an individual that could be collated with other information to identify them constitutes personal information. There are some prominent examples:
- a person’s name and/or surname
- somebody’s home address
- a personal phone number
- a passport or ID number
And some less obvious ones:
- an email address that contains the user’s name and surname (i.e. smith@gmail.com)
- a browser cookie ID
- an IP address
- the advertising ID of a mobile device
- location data from a phone or GPS device
- the presence of a particular substance in someone’s blood
- opinions or assessments about a person
- economic or social behavior of a person
In other words, when the EU says “any, ” it means any. You must make your own assessment in this regard, as no list can cover every scenario.
 What is sensitive personal data under GDPR?
What is sensitive personal data under GDPR?

Certain types of personal data are considered sensitive and therefore should not be processed unless they meet certain conditions. Such data is usually considered potentially damaging to a person’s safety or freedom of expression. In this case, the EU does provide a specific list:
- personal data revealing racial or ethnic origin, political opinions, religious or philosophical beliefs
- trade-union membership
- genetic data or biometric data processed solely to identify a human being
- other health-related data
- data concerning a person’s sex life or sexual orientation
- details surrounding convictions and criminal offenses
 GDPR and anonymized data
GDPR and anonymized data

If personal data has been anonymized, it is naturally not subject to GPDR. However, it is common for organizations to misunderstand what exactly constitutes anonymized data.
The GDPR definition of anonymized data follows the EU’s data protection laws. They state that anonymous data is “information which does not relate to an identified or identifiable natural person or to personal data rendered anonymous in such a manner that the data subject is not or no longer identifiable.”
The critical thing to note is that a subject is still considered identifiable if the processed data can be combined with additional information about them to identify them. This is referred to as “pseudonymization”. Encryption, too, is considered pseudonymization, since secret keys are “additional information” that would enable identification.
 What are the GDPR data security requirements?
What are the GDPR data security requirements?

GDPR personal data must be processed in a way that ensures appropriate security. This includes protection against unauthorized and unlawful processing/access but also against accidental leakage or loss. GPDR does not list specific technologies, stating only that “appropriate technical or organizational measures” must be used to ensure integrity and confidentiality. You must be able to demonstrate compliance with this.
Data retention and GDPR
GDPR states that personal data must be stored for the shortest time possible. This length of this period depends on why an organization needs the data and any legal obligations it has regarding retention. Retention periods must be proportionable and appropriate, and organizations should set time limits to erase or review stored data.
GDPR: what are the considerations for deletion of data?
GDPR states that you must also have systems to ensure that outdated or inaccurate data is erased or rectified without delay. Additionally, companies are obligated to delete personal data on a user should they request it.
 Enforcing GDPR security policies with DRM
Enforcing GDPR security policies with DRM
The Locklizard document security approach, working with the Adobe PDF format, is to encrypt PDF files and then apply DRM controls. We use PDF because it was designed to maintain the form and format of the original document. The beauty of PDF is that you can easily convert any document to it without losing its original vision.
Encrypting documents and applying DRM makes personal data unprocessable. So you don’t need to restrict document forwarding or worry about users copying protected documents. Stealing a DRM encrypted PDF achieves nothing because it cannot be read without a license from the supplier. The user must have either our secure viewer installed on a licensed machine, or a valid login to a web portal holding and serving the encrypted document to authorized users. With Locklizard installed Viewers, there are no passwords for users to enter or share with others, and documents are locked to devices. You can even control the locations from which users can open protected documents (i.e., an office location so that sensitive documents cannot be taken out of the building) or, more generally, restrict document access to a country.

Protecting documents with DRM is easy. Let’s go through the steps in the process to protect documents and for users to receive protected documents from you.
- Save your documents containing personal information to the PDF format using your software of choice. For example, here is how to convert Word to PDF.

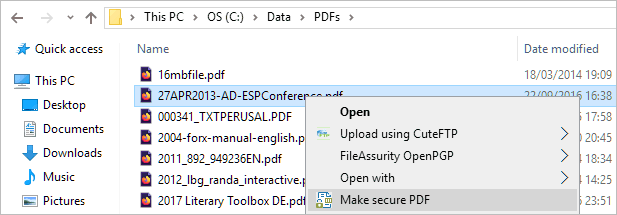
- In Windows File Explorer, select your PDF files that need protecting, right-click on them, and choose the ‘Make Secure PDF’ option from the menu.
%22%20transform%3D%22translate(1.2%201.2)%20scale(2.41016)%22%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-.5809%2027.73216%20-106.81608%20-2.23748%20197.3%200)%22%2F%3E%3Cellipse%20rx%3D%2246%22%20ry%3D%2230%22%2F%3E%3Cellipse%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(84.31433%2010.80091%20-3.55798%2027.77434%20176%200)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- From the Safeguard Writer GUI, select the controls you want to apply (i.e., expire after a number of days use, watermark document with user details, stop printing, stop screen grabbing, log document views, etc.). Once you have selected your controls, press the Publish button. You will now have protected documents (encrypted and with DRM protection) that mirror the unprotected PDF files.
%22%20transform%3D%22translate(1.3%201.3)%20scale(2.57031)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%234b8fc5%22%20cx%3D%2284%22%20cy%3D%227%22%20rx%3D%22194%22%20ry%3D%2215%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-132.31977%2038.04086%20-24.81465%20-86.31426%20103.4%20134.4)%22%2F%3E%3Cellipse%20fill%3D%22%23d4d1cf%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(82.1%20-70.5%20201.8)%20scale(28.42074%20194)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- Decide how to distribute your protected documents. Because the documents are encrypted, they may be stored anywhere without the risk of the data being extracted or processed by anyone without a license. You could make them freely available from your website, distribute them by email, USB, etc.
%22%20transform%3D%22translate(1.3%201.3)%20scale(2.60547)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23197dcd%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-220.9407%202.06484%20-.3131%20-33.50216%20162.2%200)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-28.43406%2080.74288%20-237.41098%20-83.6056%20242%20168.6)%22%2F%3E%3Cellipse%20fill%3D%22%23cecac8%22%20cx%3D%2278%22%20cy%3D%2244%22%20rx%3D%22252%22%20ry%3D%2218%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
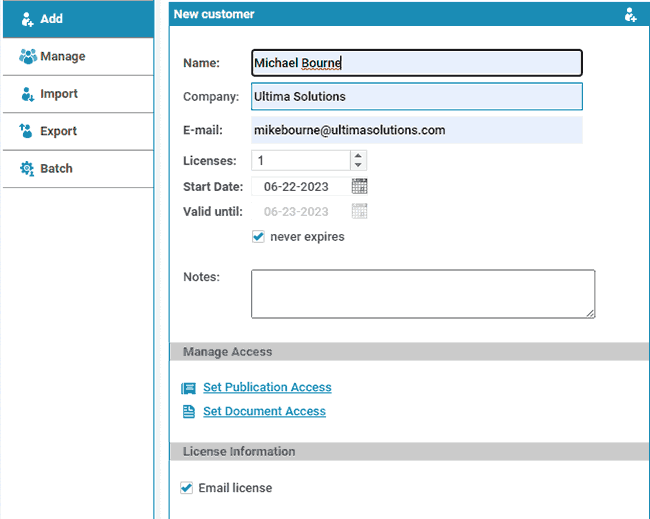
- Log in to the web-based Safeguard Administration system and add the users you want to be able to access the secured document(s). This is a simple action of adding their name, company (optional), and email address and then selecting which documents (or groups of documents) you want them to be able to access.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%235dbfa0%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(510.05773%20-14.95746%201.30653%2044.55327%20256.1%2011.2)%22%2F%3E%3Cellipse%20fill%3D%22%23d3ced0%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(372.3371%20-6.67886%20.9734%2054.2654%20283%2087.7)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(-94.9%20341.6%2015.9)%20scale(209.55754%20647.46081)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
- The Admin system automatically emails recipients with a link to download the Viewer and their license. Once users have installed the Viewer and clicked on their license file, they can open any documents you have authorized them to view. The license registration is a one-time use (unless you authorize more), so if users forward their registration email to others, they won’t be able to use it.
 Automating GDPR compliance by securing documents
Automating GDPR compliance by securing documents
A simple way to enforce your company document protection policies and ensure you comply with GDPR is to use Safeguard Command Line to automate the GDPR document security policies you want to apply. This is as simple as:
- Creating batch files with the DRM controls you want to apply to specific document types.
- Creating folders on your disk where users store different types of files according to their confidentiality status.
- Using Windows Scheduler to automate when batch files are run and your documents protected.
Safeguard Command Line is also helpful if you have many documents to protect, since they can be processed automatically in one go.
 GDPR Data Protection & control of sensitive data
GDPR Data Protection & control of sensitive data

 GDPR and data sharing
GDPR and data sharing
There are certain GDPR file sharing requirements, particularly regarding sharing data with third parties. Primarily, data must be shared in line with your terms of service and on a lawful basis (i.e., with consent). Sharing should be reasonable, proportionate, and transparent. The organization is of course the one responsible for ensuring that employees do not share or leak personal data.
Some companies say that using a browser rather than installing software allows authorized users to view protected documents more easily. This may be true, but it also makes it easier for unauthorized users to compromise them. If you rely on a browser-based system for document protection and GDPR compliance then be aware that:
- Users can share login details with others (and therefore access to all your secure documents).
- Browser security is inherently weak with only JavaScript and obfuscation being the only tools to stop users removing the document protection.
- Browser-based technology cannot stop third-party screen grabber tools or printing to PDF format (if printing has been allowed).
- Users may end up using an unauthorized browser that does not obey the DRM controls that have been applied (like preventing copy and pasting of text).
No doubt the hosting infrastructure of these companies is secure, but if users can share login details or you’re using web-based document controls, anyone can access your protected documents.
 So why are my documents more secure with Locklizard?
So why are my documents more secure with Locklizard?
Locklizard does not force you to upload your unprotected documents to our servers. This is because protecting documents on a server presents issues if the encryption process fails or temporary files are created and not deleted. Instead, you protect documents locally on your computer and maintain complete control over them. Your protected documents can be distributed just like any other file; only authorized recipients can view them, no matter who they are forwarded to.
Your documents are encrypted with AES encryption both in transit and at rest. All user information held on our administration systems (either hosted by you or by us) is encrypted to ensure GDPR compliance if the database were ever breached.
 The best way to achieve GDPR compliant file sharing for PDFs
The best way to achieve GDPR compliant file sharing for PDFs

GDPR states that you must ensure that personal and sensitive data are protected from theft and that data must not be held for longer than is necessary for the declared purpose. Though not an explicit requirement of GDPR, demonstrating the prevention of further data processing by denying document use shows that you take data security seriously. Additionally, preventing ready transfer to unregulated systems for unauthorized processing is a very good way to indicate that you exceed minimum requirements.
Locklizard document protection ensures you can demonstrate that you have complied with and exceeded GDPR compliance and data protection policies. You can:
- protect documents with expiry dates so they can no longer be accessed after the pre-set end date is reached
- protect documents with limited views so that sensitive data can only be viewed a set number of times before it expires
- protect documents with limited prints so that multiple high-quality printouts cannot be made to redistribute data
- revoke documents at any time in the event of loss or change to authority (a mandatory deletion, for instance)
- enforce document use in specific locations, preventing use in areas that are not considered to have appropriate security
- log document use so you can be certain who has viewed and/or printed sensitive data
- ensure that only authorized parties can access the documents
To secure your users’ personal data and achieve GDPR-compliant file sharing, take a 15-day free trial of our PDF DRM software.

 GDPR and data security
GDPR and data security GDPR: What information needs to be secured?
GDPR: What information needs to be secured? What is personal data under the GDPR?
What is personal data under the GDPR? What is sensitive personal data under GDPR?
What is sensitive personal data under GDPR? GDPR and anonymized data
GDPR and anonymized data What are the GDPR data security requirements?
What are the GDPR data security requirements? Enforcing GDPR security policies with DRM
Enforcing GDPR security policies with DRM


 Automating GDPR compliance by securing documents
Automating GDPR compliance by securing documents GDPR Data Protection & control of sensitive data
GDPR Data Protection & control of sensitive data GDPR and data sharing
GDPR and data sharing So why are my documents more secure with Locklizard?
So why are my documents more secure with Locklizard? The best way to achieve GDPR compliant file sharing for PDFs
The best way to achieve GDPR compliant file sharing for PDFs
